Turns out, the Windows registry is not as scary as everyone makes it out to be. Granted, if you do not know what you are doing, there is ample opportunity for you to severely mess up installed software and the operating system itself. But not only is it simple to fix (backups, backups, backups!), you would also have to be fairly careless in what changes you were making. It is not possible to detect side-by-side installations of both 64-bit and 32-bit versions of Python prior to 3.5 when they have been installed for the current user. Python 3.5 and later always uses different Tags for 64-bit and 32-bit versions. Is the root of settings for the currently logged-in user, and this user can generally read and write all settings under this root.
- S0167 Matryoshka Matryoshka can establish persistence by adding Registry Run keys.
- Each computer in the chain has these Registry entries.
- Additionally, Microsoft Edge shipped with the “Internet Explorer mode” feature, which enables support for legacy internet applications.
- After installing the below updates, the CPU usage is high and remains high even when the machine is idle.
You can lock the value if program cant start because riched32.dll is missing you don’t want users to be able to change the value in the Policy Editor. The statement you provide is like the control name that describes what it is and how it should be implemented in the environment. You’ll also need to decide which category the control belongs to. This is important because users can search and filter controls by category, they can also search by keywords in the statement.
The author believes that this constitutes a “fair use” of any such copyrighted material as provided for in section 107 of the U. In accordance with Title 17 U.S.C. Section 107, the articles published on this website are distributed without profit for research and educational purposes. All material on this website is posted in accordance with the limitations set forward by the Digital Millennium Copyright Act . All information on this site are provided “as-is” without warranty of any kind.
window.onerror = process;
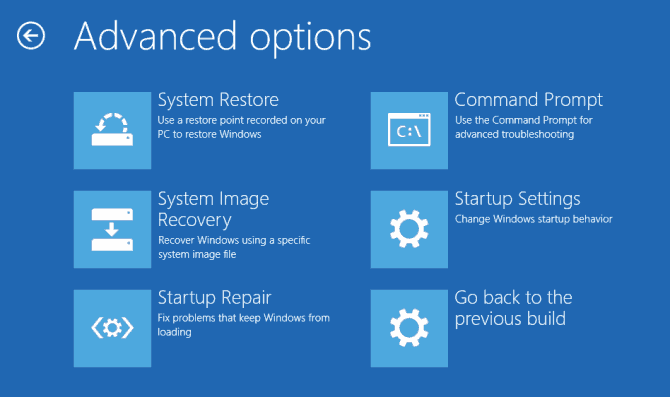
You can force this by restarting your PC and pressing theF11 or F8 key before the spinning cursor appears. If this registry setting is present and non-zero, then EFT Server determines if an upload will delete an existing file. If a file already exists, EFT Server does an additional check for Delete permission. This registry key determines whether EFT Server checks for the “Delete” permission when a client uploads a file. The Event Rule Monitor Folder process is limited to 3 concurrent threads by default.
How to Edit Registry in Windows 10 & 11?
Once the process is completed, restart your computer. It will search for and replace corrupted operating system files if any are found.
DLL files contain numerous functions, classes, and variables that other programs can use as and when the need arises. This works natively on Linux, but requires the installation of a compatible driver on Windows using Zadig. While playing, if yuzu needs to translate a new shader, the game will stutter. Loading into a game for the first time can give long freezes due to the number of shaders. As you keep playing, the amount of stuttering will decrease.
Writing External Functions
Otherwise, you will get an error screen saying “updates not installed” when you try to access IE. This is another common error that comes when you have overloaded the Web browser with many tabs that may need an additional amount of processing power, which the computer may not handle. Therefore, the web browser shows the failure to alert the user of a freeze/hang of the software. The way to fix this is by avoiding overloading your browser with multiple tabs all at once. Alice Woods- Shares the knowledge about computer protection Alice Woods is a security expert who specializes in cyber threat investigation and analysis. Her mission on Ugetfix – to share the knowledge and help users to protect their computers from malicious programs. This patented repair process uses a database of 25 million components that can replace any damaged or missing file on user’s computer.
Since no path is given, the process launches from the windows storage location, the \Windows directory. Winlogon.exe is another user-mode executable that is loaded very early during startup by wininit.exe and handles interactive user logons and logoffs. CurrentControlSet is a subkey within the HKLM root key that is targeted by malware — when viewing some telemetry sources you may see ControlSet001 or ControlSet002 show up. This is because CurrentControlSet doesn’t actually exist — it’s a symbolic link to either ControlSet001 or ControlSet002, whichever the system is using at the time. The other is kept as a backup for the “load last known good configuration” boot option within Windows. The top reason that attackers turn to the database is persistence. There are many ways that the registry can be used by an attacker to maintain their foothold in a network.


